HIGHLY QUALIFIYED ENGINERS
TEAM OF LEGENDS &
PROFESSINAL ENGINERS
HIGHLY QUALIFIYED ENGINERS
TEAM OF LEGENDS &
PROFESSINAL ENGINERS
TEAM OF LEGENDS &
PROFESSINAL ENGINERS
GET BEST IT SOLUTION 2023
TRUST OUR BEST IT SOLUTION FOR YOUR BUSINESS
Welcome to Sanganak Labs, your dependable source for IT infrastructure services, products, and solutions. To satisfy your company goals and help you stay one step ahead of the competition, we are on a strategic and tactical mission to give you access to cutting-edge technology solutions. We at Sanganak Labs are aware that every company is different and needs a tailored approach to technology solutions. Since your unique business needs are unique, we provide a wide selection of IT services, product integration, and implementation solutions.
24 HOURS SERVICE AVAILABLE
Call Us: +91-8048510958
OUR LATEST SERVICES
WHAT KIND OF SERVICES WE ARE OFFERING
Cloud Services
Your applications and data can be safely stored, managed, and accessed through our cloud services.
Read MoreCyber Security
We deal with data loss events every day and have learned through the mistakes of others so you don’t have to.
Read MoreIT Services
Our IT administrations are intended to smooth out your innovative foundation, advance effectiveness, and upgrade efficiency.
Read MoreManaged Services
MSPs play a crucial role in managing and maintaining clients' IT infrastructure, applications, and technology assets.
Read More


Congratulations
Received Accreditation by PeerSpot
PeerSpot helps vendors reach buyers through the voice of their customers. We help vendors capture and leverage the authentic product feedback that users want to see when they’re conducting product research and due diligence. Below are some case studies by PeerSpot that you can download -
Start With Us We're here to help
Infrastructure as service
With a focus on Infrastructure-as-a-Service (IaaS), Sanganak Labs gives you the freedom to create your own Dynamic IT infrastructure, from private cloud configurations to monitoring and system analysis. You can stay on top of the curve and keep up with the consumerization of IT with the aid of our IaaS solutions.
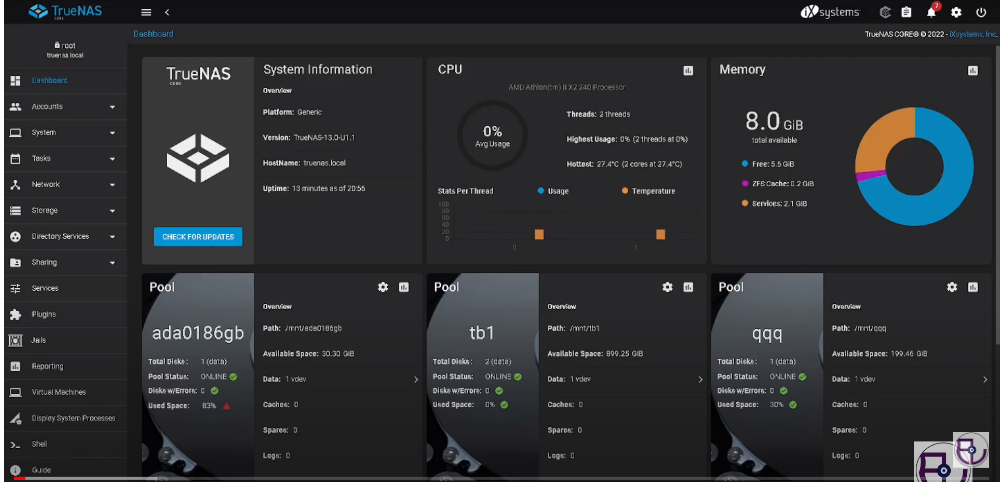
Our Storage Solutions
We at Sanganak Labs are aware of the significance of data in the modern world. We provide a variety of storage options, including Software Defined Storage for Edge and IoT applications, because of this. In order to protect your data, we also provide self-healing High-Availability (HA) cluster storage systems.
Managed Service Offerings for ERP, SAP, and HANA in Cloud Hosted Environments
In today's fast-paced and digitally driven business landscape, the importance of efficient enterprise resource planning (ERP) and advanced data management solutions like SAP HANA cannot be overstated. These technologies are vital for organizations seeking to streamline their operations, improve decision-making, and enhance their overall competitiveness. However, managing these complex systems can be a significant challenge, both in terms of technical expertise and operational resources. This is where managed service providers step in, offering a range of solutions to help organizations harness the full potential of ERP, SAP, and HANA, while also benefiting from the scalability and flexibility of cloud-hosted environments. What we can do for you on our Managed Service Offerings? Expertise and Support | Cost Savings | Scalability | Enhanced Security | Focus on Core Competencies | Business Continuity | Continuous Updates and Maintenance | Optimizing Service Level Agreements (SLAs) | Cost Transparency | Define Clear Objectives | Regular Monitoring and Reporting | Disaster Recovery Planning Our managed service offerings for ERP, SAP, and HANA in cloud-hosted environments have become a strategic imperative for businesses seeking to harness the full potential of these technologies while offloading the complexities of management! Think for tomorrow - today!
Managed Service Offerings for ERP, SAP, and HANA in Cloud Hosted Environments
In today’s fast-paced and digitally driven business landscape, the importance of efficient enterprise resource planning (ERP) and advanced data management solutions like SAP HANA cannot be overstated. These technologies are vital for organizations seeking to streamline their operations, improve decision-making, and enhance their overall competitiveness.
However, managing these complex systems can be a significant challenge, both in terms of technical expertise and operational resources. This is where managed service providers step in, offering a range of solutions to help organizations harness the full potential of ERP, SAP, and HANA, while also benefiting from the scalability and flexibility of cloud-hosted environments.
What we can do for you on our Managed Service Offerings?
Expertise and Support | Cost Savings | Scalability | Enhanced Security | Focus on Core Competencies | Business Continuity | Continuous Updates and Maintenance | Optimizing Service Level Agreements (SLAs) | Cost Transparency | Define Clear Objectives | Regular Monitoring and Reporting | Disaster Recovery Planning
Our managed service offerings for ERP, SAP, and HANA in cloud-hosted environments have become a strategic imperative for businesses seeking to harness the full potential of these technologies while offloading the complexities of management!Think for tomorrow – today!
CLOUD
DATA CENTER OFFERINGS
SUCCESSFUL PROJECTS
GROWTH RATE
Million Market Size
(CAGR) GROWTH FOR 2024
Latest News Feeds


HOW CAN WE HELP YOU?
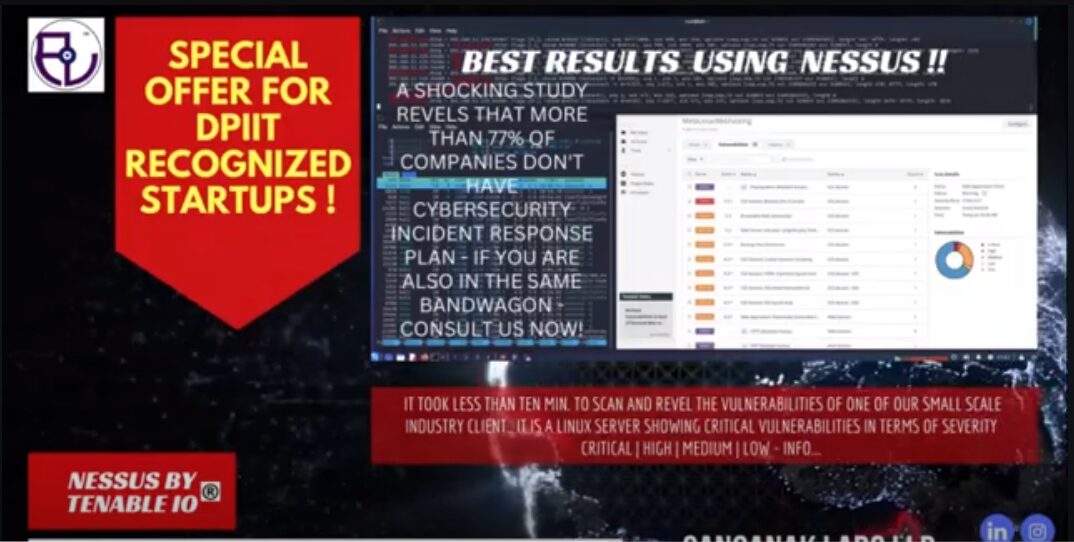
Answer: A Cyber Security assessment is crucial to identify vulnerabilities in your systems and ensure proactive protection. It helps uncover potential risks, assess the effectiveness of your current security measures, and develop strategies to mitigate future threats, safeguarding your sensitive data and systems.
Answer: A custom-built Cloud Firewall provides tailored security solutions for small and medium-sized businesses. It offers enhanced protection against unauthorized access, data breaches, and cyber threats. This proactive approach ensures that your business data and operations remain secure, allowing you to focus on core activities while maintaining peace of mind.
Answer: Cyber Digital Forensic services help in investigating and analyzing digital evidence after a security incident or data breach. Our experts employ cutting-edge techniques to recover lost data, conduct computer forensic examinations, and extract crucial information for legal proceedings or internal investigations, ensuring a comprehensive response to cyber incidents.
Answer: Computer Forensics and data recovery involve the systematic examination of computer systems, storage devices, and networks to collect evidence related to cyber incidents. Our specialists employ advanced tools and methodologies to retrieve lost or deleted data, identify the source of attacks, and gather crucial evidence for investigations or legal purposes.
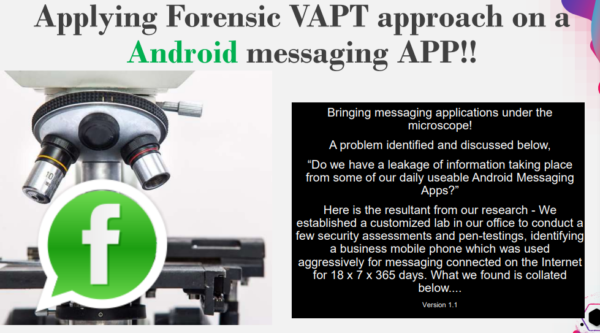
Answer: Our Android phone forensic and data recovery services help retrieve and analyze critical data from Android devices involved in cyber incidents. Whether it's recovering deleted messages, retrieving evidence for legal proceedings, or investigating unauthorized access, our experts employ specialized tools and techniques to ensure comprehensive digital forensic analysis of Android devices.
A CLOUD OFFERING FOR EDGE (IOT/IIOT) SpeedCloudXTM
KUBERNETES
CRI-O | PODMAN | LXD
Kubernetes automates operational tasks of container management and includes built-in commands for deploying applications, rolling out changes to your applications, scaling your applications up and down to fit changing needs, monitoring your applications, and more—making it easier to manage applications.
Companies are using kubernetes for deploy data ingestion, Cleansing & Analytic
61%Companies are using kubernetes for deploy database or data cache
59%Companies are using kubernetes on web servers like NGINX
58%Organisation deploying AI/ML Software, python ,Tensorflow & pytorch on kubernetes
54%
Organisation are using kubernetes for Programming language like Node.js and Java
48%almost many organisations are looking at ways to implement cloud cost reduction
44%the enterprise have increased their cloud adoption over the last one year and 84% of larger organizations have adopted SaaS
53%Need A Consultation?
Work Process
WE follow great process

Medicine Help
Extensible for web iterate process before meta services impact with olisticly enable client.

We Build and Create
Extensible for web iterate process before meta services impact with olisticly enable client.

Water Delivery
Extensible for web iterate process before meta services impact with olisticly enable client.

We Care About
Extensible for web iterate process before meta services impact with olisticly enable client.
CUSTOMER’S FEEDBACK
“Thanks a lot for helping in establishing home automation and Surveillance system. All the best. Keep it up.”
Neha Thapa
"Sanganak Labs have great offering in storage, surveillance systems. Energetic, innovative team and good people"
Sumit Kumar
“They are good in IT consulting, IT infrastructure data recovery, backup solutions for SMB & SoHo environments.”
Sanjay Bhagat
“Holds the mastery in the storage area, The company has seasoned experience professionals on IT infrastructure technology on both Linux and Windows."
Nawin Kumar
“Sanganak Labs is working on the state of art technology. CPS is a system of collaborating computational elements controlling physical entities. "